8 minute read
Dear Phil,
We had some questions concerning the invoice sent on May 5, 2020, for our
x-ray equipment. Specifically, we discussed with our salesman that we would
receive a discount for the item on line 24 of the invoice. Please view the
invoice here.
Thank you,
Jane
Doe
XYZ Imaging Center
Looks like a pretty safe email, right? Aside from the name of the person sending
it and the name of the imaging center, which I changed to anonymize the email,
this looks pretty legitimate. Specifically, it addresses me individually, it is
from a known customer, it references x-ray equipment, and the email headers (not
shown) were from a real customer that we do business with regularly. So when
this email landed in my inbox, I, at first, thought the sender had sent it to
one of the other mailboxes that I monitor for the company. My first thought was
to forward the email to the sales representative and CC our accounting
department. But after seeing that the email was sent directly to me, the
marketing manager, the email made me very suspicious.
Let me back up a
little and explain that CMS Imaging, like every company, takes our email
security very seriously. We use a few different cybersecurity products to assist
in our protection, and typically, the emails that land in our inboxes are more
often than not legitimate. But the best cybersecurity tools can be fooled (big
thanks to our Chief Technology Officer for all the reminders). I know that the
best defense is to be cognizant of the attachments I open and the links I
follow. I chose to contact the people who do cybersecurity for us and let them
investigate the email before I opened it.
My suspicions were confirmed
very shortly after I contacted our cybersecurity people. While it may seem
pretty obvious in hindsight, this email was an attempt to steal my credentials
and transmit ransomware and give the bad actors the ability to send similar
emails to my contacts. The truly devious part about this email was that the bad
actors (I really would like to call them something else, but this is a business
blog post) had designed this email to fool most email cybersecurity software.
Because they had access to our client's email, they also had access to their
cloud drive. The email link would have directed me to our client's legitimate
cloud drive, which was safe. But to view the invoice, I would have needed to
enter my credentials to access the details of the invoice and see line 24. The
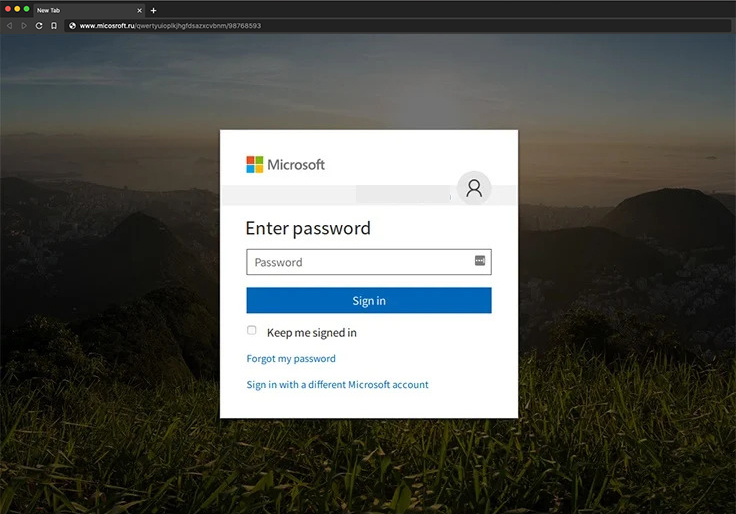
URL link to enter my credentials was "micosroft.ru/qwerty/98768593" (the
micosroft.ru is real, but the rest is fictitious.) The bad actors were hoping
that a glance, I would have mistaken the primary domain of the URL for
"microsoft.com." Because the link on the original email sent me to a legitimate
URL and the sender had previously sent legitimate emails to our domain, none of
our email cybersecurity products would have picked up that this was an attempted
spear-phishing attempt.
So what would
have happened if I had clicked the links and entered my credentials?
Probably nothing, at least right away.
I would,
more than likely, have received a "Page Not Found" error. And after several
attempts, I probably would have chalked this up to a human error and given up on
viewing line 24 and went about my day. But unbeknownst to me, this bad actor
would have signed into my email account and begun reading my emails to learn
more about my contacts. They would then start crafting emails targeting my
contacts and including real details about previous communications.
Simultaneously, their partners (typically these are no longer kids in their
parent's garages, but organized syndicates) would than begin creating and
inserting a fake link in a document that would direct the recipient to
"micosroft.ru/qwerty/98768593." They would also create rules in my email inbox,
marking any incoming emails with the subject line of the email they are about to
send as "Read" and moving the email to my "Trash." Within a few business days,
they would send the emails, and they would activate their ransomware.
If
you are unfamiliar with ransomware, it is a short bit of code that encrypts a
server's contents. They would, in essence, place a password over the contents of
a server that would delete all of the emails and documents stored on that server
after a certain amount of incorrect attempts. For the bad actors to enter the
password and remove the encryption, they would charge a ransom of up to $1M.
According to Emsisoft * in 2019, there were 113 federal, state and municipal
agencies, 764 healthcare providers, and 89 schools and universities in the
United States.
But paying the ransom does not always guarantee that the
bad actors will enter their password. "The FBI does not advocate paying a
ransom, in part because it does not guarantee an organization will regain access
to its data. In some cases, victims who paid a ransom were never provided with
decryption keys. In addition, due to flaws in the encryption algorithms of
certain malware variants, victims may not be able to recover some or all of
their data even with a valid decryption key." **
So what should a
healthcare facility do if they are the victim of
ransomware?
The Centers for Medicare and Medicaid
Services requires that any healthcare facility that accepts Medicare and or
Medicaid adhere to their Emergency Preparedness Rule. In short, the medical
facility must have a plan to deal with all emergencies (fire, flood, hurricane,
cybersecurity breaches, acts of violence ...) and train and test its employees
on emergency procedures. This plan will include each employee's responsibilities
in the case of varying emergencies. With ransomware, the HIPAA Privacy Rule is
in effect because compromised information in a ransomware attack may consist of
Protected Healthcare Information (PHI).
Would you know
what to do if you received this email? If not, now is an excellent time
to start asking questions.
- * Emisoft.com. (2019). The State of Ransomware in the US: Report and Statistics 2019 [online] Available at: https://blog.emsisoft.com/en/34822/the-state-of-ransomware-in-the-us-report-and-statistics-2019/.
- ** Federal Bureau of Investigations. HIGH-IMPACT RANSOMWARE ATTACKS THREATEN U.S. BUSINESSES AND ORGANIZATIONS. Available at: https://www.ic3.gov/media/2019/191002.aspx.








 ©
- CMS Imaging, Inc. All Rights
Reserved
©
- CMS Imaging, Inc. All Rights
Reserved

Comments
Leave a Comment