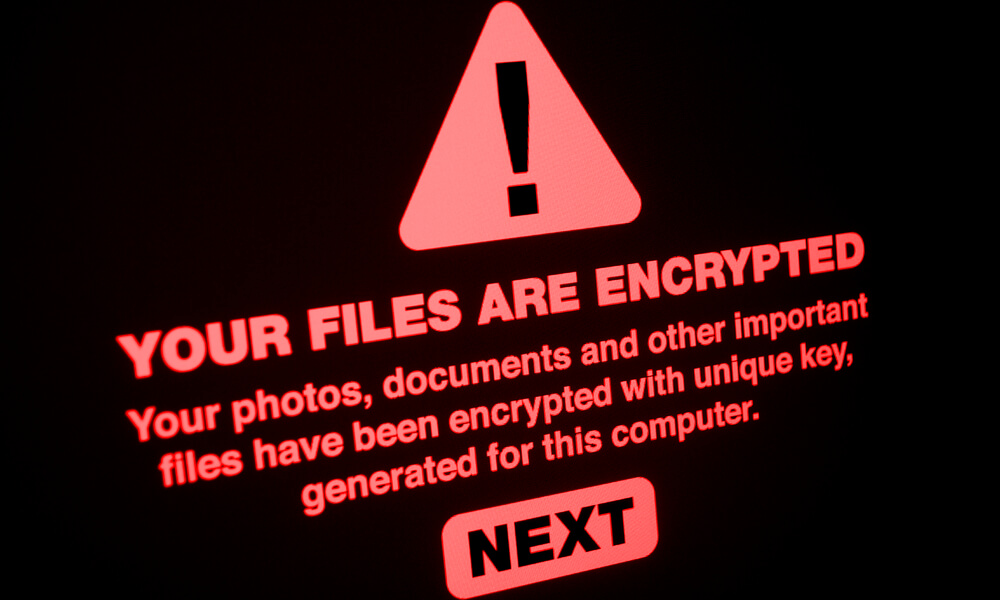
On Wednesday, November 27, 2019,
Great Plains Health, a hospital system in Nebraska, fell victim to a
ransomware attack shutting down all hospital computer systems and forced
the hospital to cancel all non-emergency procedures.
On Thursday,
December 12, 2019, Southeastern Minnesota Oral and Maxillofacial Surgery
(SEMONS) reported a ransomware attack that may have exposed the Personal
Health Information (PHI) of their patients. On September 23, 2019,
hackers attacked a server used by SEMONS in a ransomware attack. The IT
department intervened immediately and was able to restore the data
quickly. SEMONS did not report a ransom demand or money paid to the
hackers, but the facility had to inform their 80,000 patients of the
threat.
On Friday, December 13, 2019, the City of New Orleans
suffered a severe cyberattack, which led Mayor LaToya Cantrell to
declare a state of emergency. The city's IT department immediately gave
the order for all city employees to power down their computers and
mobile phones and disconnect from WiFi. Additionally, the city servers
were removed from their power sources to isolate the malware. The city's
health department continues to have limited access to patient
information, causing officials to reschedule appointments.
Do I have your attention yet? Here are three cyberattacks impacting the healthcare industry in the last month.
It seems that every day, the news media reports on a new cyberattack. Healthcare
facilities and government agencies are amongst the most provocative targets for
these cyber-criminals. Typically the criminals are hoping to extort a ransom
from the victim. But aside from the ransom, the victim is often paying much more
than the extorted payment.
The Ponemon Institute conducts independent research on data protection and
emerging information technologies. Ponemon's 'Cost of Cybercrime Study'* averages the
cost of cybercrime at $13,000,000 per organization. This amount reflects a 12%
increase from 2018. Healthcare facilities face the additional burden of a HIPAA
violation should they suspect a breach of PHI.
The Department of Health
and Human Services (HHS) added provisions for the unauthorized exposure of PHI
in the HITECH Act in 2013. These provisions mandate a facility report to HHS,
the Center for Medicare and Medicaid Services, and the patients any actual or
suspected breach that may include PHI. The fines and charges for HIPAA
violations regarding data breaches fall into two major categories: Reasonable
Cause (penalties from $100 to $50,000 per incident with no jail time for named
parties) and Willful Neglect (penalties from $10,000 to $50,000 per occurrence
and can result in criminal charges.) Additionally, the HITECH Act allows a
state's Attorney General to levy fines and seek attorney fees on behalf of the
victims. (The California Consumer Privacy Act allows the Attorney General to
penalize a covered entity $50,000 for each violation.) Courts can now also award
damages and associated costs to a person who's data is exposed.
How can we defend against these attacks in 2020?
Employee training is paramount to proper data
security. Some estimates show that 90% of all data breaches occur due to human
error. Cybercriminals send millions of emails trying to get one person to make a
mistake and allow them into their server system. People are, therefore, the
weakest link to cybersecurity defenses. There are numerous software training
programs and third-party vendors available to assist an organization with
employee training. I have covered this topic in some previous blogs (here and
here.)
But in the ever-changing digital landscape, facilities
must not
only stay current on employee training; they must keep current with the various
rules regarding healthcare data and attempt to stay ahead of the cyber-threat.
Recommendations from experts generally start with having a NIST-based (National
Institute of Standards and Technology) risk security analysis. This analysis
will establish a baseline and allow the organization to understand what it must
do to become and stay compliant.
Next, an organization must examine its
network and implement an early detection framework. Then once this security
framework is in place, test it to see how the framework addresses different
types of attacks and apply the learning from those tests. Consistent testing
will ensure the individuals responsible for the protection of your network know
what to do should an attack penetrate your servers.
Lastly, it is always
a good idea to evaluate the cyber insurance coverage and understand the
requirement and restrictions of the policy.
Unfortunately, the odds are
against our security teams, whom we expect to operate flawlessly. But with
thousands of devices in a healthcare network and as many users, these
professionals cannot be everywhere at all times. Investment in cybersecurity
software, training, and vigilance are necessary to stay over the next decade.








 ©
- CMS Imaging, Inc. All Rights
Reserved
©
- CMS Imaging, Inc. All Rights
Reserved

Comments
Leave a Comment